Here is a player’s manual to UK online casino banking options. The UK online casino landscape has transformed dramatically over the past decade, with payment...
Cyber Security
Here, I will talk about the transformative impact of Artificial Intelligence on surveillance and safety. Artificial Intelligence (AI): it’s not just a buzzword or the...
In this post, I will talk about protecting your predictive edge from digital threats. Every data-driven decision you make—whether in sports betting, finance, or business—relies...
In this post, I will show you how digital training programs support skills in healthcare settings. Healthcare workers should keep updating their information to provide...
In this post, I will answer the question – Are UK online casinos safe? Read on as I give you this guide to choosing a...
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Microsoft Office and Microsoft Windows flaws to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure...
In this post, I will discuss the no-contract Internet plans Georgia comparison. Also, I will talk about their speed, price & fees side-by-side. Georgia internet...
CVE-2026-21643: Critical FortiClient EMS Vulnerability Enables Unauthenticated Remote Code Execution
Shortly after our recent coverage of high-impact FortiOS SSO zero-day exploitation (CVE-2026-24858), defenders are facing another urgent patching priority in the Fortinet ecosystem. On February...
In this post, I will talk about the top business card makers of 2026 for quick, professional results without design experience. Business cards remain a...
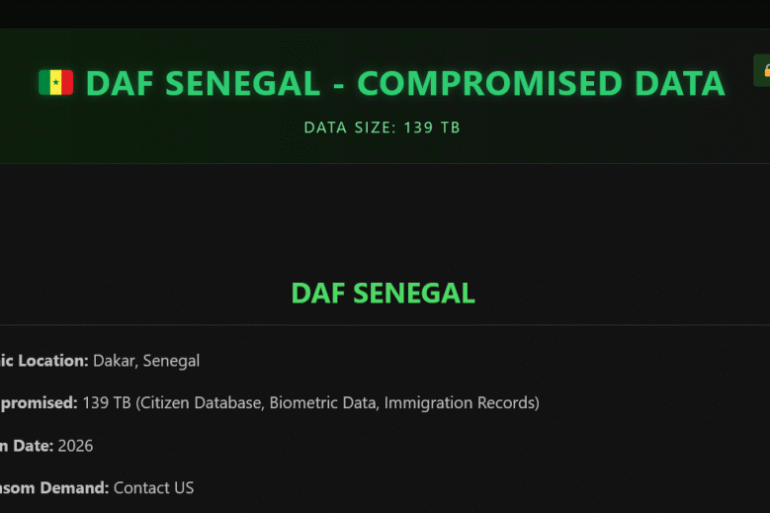
Senegal closed its national ID card office after a ransomware cyberattack disrupted ID, passport, and biometric services. Senegal confirmed a cyberattack on the Directorate of...
Dutch agencies confirmed attacks exploiting Ivanti EPMM flaws that exposed employee contact data at the data protection authority and courts. Dutch authorities said cyberattacks hit...
China-linked group UNC3886 targeted Singapore ’s telecom sector in a cyber espionage campaign, Singapore’s Cyber Security Agency revealed. Cyber Security Agency of Singapore (CSA) and...