In this post, I will show you how to erase backgrounds in seconds with the 100% free tool. Background removal is no longer a skill...
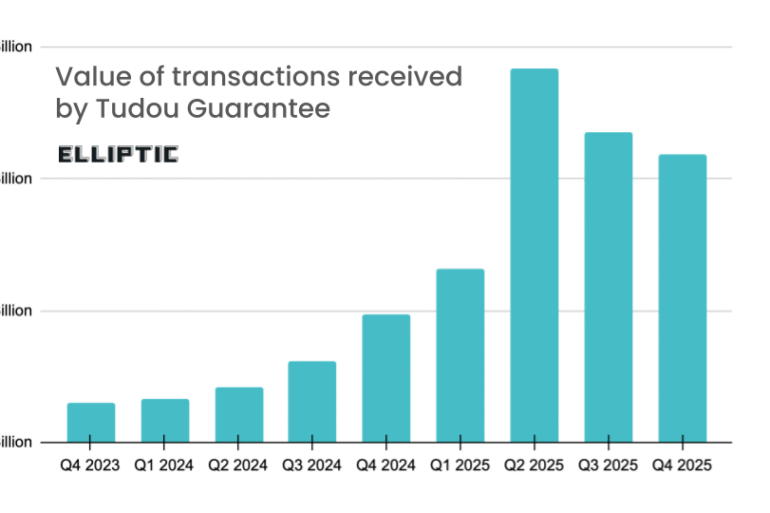
Major Telegram-based illicit marketplace Tudou Guarantee appears to be shutting down its operations, according to Elliptic. Blockchain cybersecurity firm Elliptic reports that Tudou Guarantee, a...
Explore the top WordPress LMS plugins for 2026. Compare features, pricing, and ideal use cases to find the best learning management system for your website....
The UK government warns Russia-linked hacktivists are still carrying out DDoS attacks on critical infrastructure and local government systems The UK government warns that Russia-linked...
In this post, I will show you how specialized IT for banks is evolving to combat operational risks. The modern financial landscape is a minefield...
In this post, I will talk about bridging the gap between patient care and advanced data encryption standards. As a Practice Manager, you wear many...
In this post, I will talk about the evolution of location-aware authentication for mobile workforces. Managing a distributed workforce is one of the most complex...
Remember Heartbleed? That security nightmare from a few years back that made everyone panic about their passwords? Well, meet its distant cousin: MongoBleed. And if...
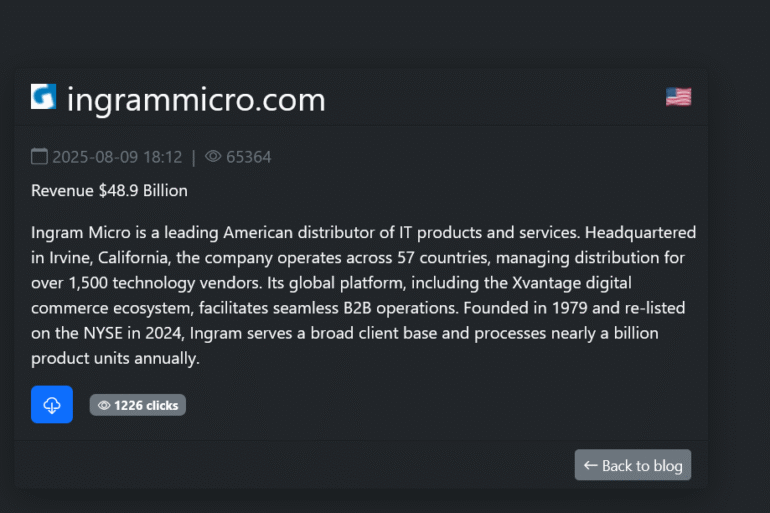
Ingram Micro says a ransomware attack exposed personal data of about 42,000 people, including names, birth dates, SSNs, and job-related details. Ingram Micro is a...
In this post, I will show top 10 data masking techniques enterprises use to prevent large-scale data breaches. Data breaches present a major threat to...
In this post, I will give you practical steps to avoid loan scams when borrowing online. In today’s digital age, borrowing money online has become...
In this post, I will talk about understanding access control systems and security management. In today’s fast-paced world, ensuring the security of assets, data, and...