Shortly after Microsoft’s massive January Patch Tuesday release addressing the CVE-2026-20805 zero-day vulnerability in Windows Desktop Window Manager, another technology giant has issued a security...
Cisco fixed a maximum severity AsyncOS flaw in Secure Email products, previously exploited as a zero-day by China-linked APT group UAT-9686. Cisco fixed a critical...
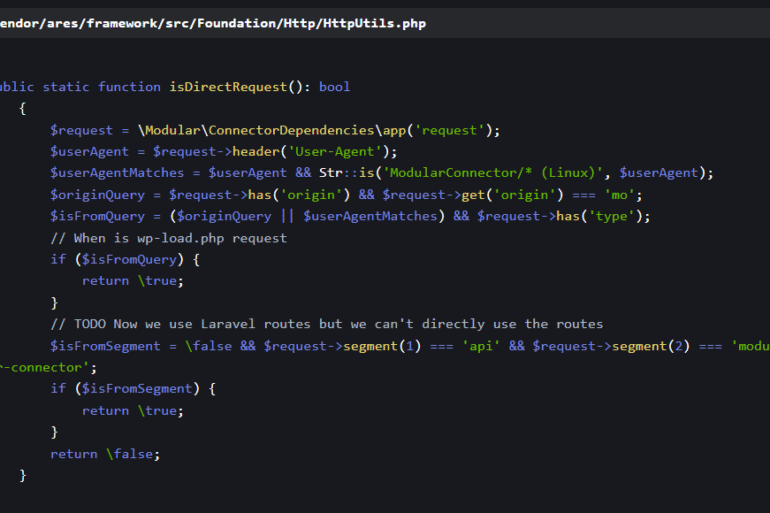
A critical Modular DS WordPress flaw (CVE-2026-23550) is actively exploited, enabling unauthenticated privilege escalation. Threat actors are actively exploiting a critical Modular DS WordPress vulnerability...
In this post, I will talk about when social gaming becomes a security vulnerability. Social gaming has turned casual play into a global phenomenon, drawing...
South Korean conglomerate Kyowon confirmed a ransomware attack that disrupted operations and may have exposed customer data. Kyowon Group is a major South Korean conglomerate...
In this post, you will learn how much private tutoring cost in Fremont, CA. For parents in Fremont, CA, considering additional academic support for their...
In this post, I will talk about what the Agile transformation journey involves. In today’s fast-paced business environment, organizations are under constant pressure to respond...
In this post, I will show you how non-profits can use free AI video tools for fundraising. For many non-profit organizations, the biggest hurdle to...
A cyberattack on Central Maine Healthcare exposed the personal, medical, and insurance data of about 145,000 patients. Central Maine Healthcare notified patients affected by a...
In this post, I will talk about data breaches & rising cyber Threats in Sports tech. I will also address this subject from Football Australia...
API security is becoming more important by the day and skilled practitioners are in high demand. Now’s the time to level up your API security...
As 2026 gets underway, the pace of critical vulnerability disclosures shows little sign of easing. Following the recent MongoBleed (CVE-2025-14847) revelation, Microsoft has kicked off...