Palo Alto Networks addressed a flaw impacting GlobalProtect Gateway and Portal, for which a proof-of-concept (PoC) exploit exists. Palo Alto Networks addressed a high-severity vulnerability,...
China has told domestic firms to stop using U.S. and Israeli cybersecurity software, citing national security concerns amid rising tech tensions. Reuters reported that China...
Smart technology has become an essential part of modern property management. Property owners and managers rely on digital tools to handle daily responsibilities with more...
On January 12, 2026, the CERT-UA team disclosed a targeted cyber-espionage campaign against the Ukrainian Armed Forces that abused charity-themed social engineering to deliver the...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds a flaw impacting Microsoft Windows to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure...
In this post, I will talk about dedicated development teams for Startups. Also, I will discuss its benefits and costs. A dedicated development team is...
In this post, I will show you the SafeLine Firewall review. Also, I will give you the step-by-step deployment guide. In the ever-evolving landscape of...
In this post, I will talk about fast-tracking safety by using custom pharmaceutical labels for high-speed lines. In the pharmaceutical industry, the margin for error...
Learn how online content removal is colliding with open-record laws in this post. A public official’s embarrassing email appears online after a lawful public-records request....
Remember 2020? We scanned QR codes for everything. Restaurant menus. Parking meters. That awkward moment at a wedding when someone wanted you to scan a...
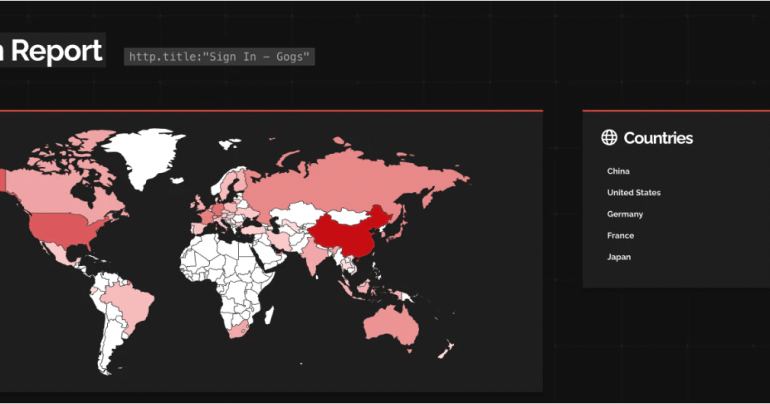
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds a flaw impacting Gogs to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security...
In this post, I will talk about the future of smart clothing and scarves. Wearable technology is now a key aspect of how we live. From...