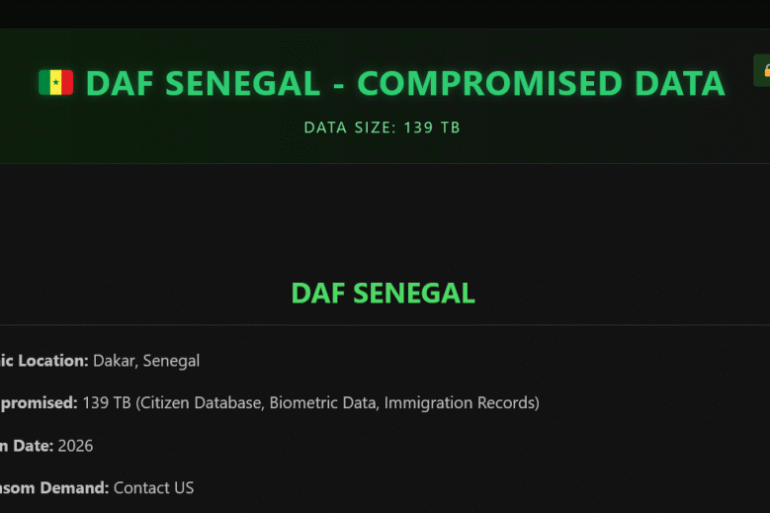
Senegal closed its national ID card office after a ransomware cyberattack disrupted ID, passport, and biometric services. Senegal confirmed a cyberattack on the Directorate of...
Dutch agencies confirmed attacks exploiting Ivanti EPMM flaws that exposed employee contact data at the data protection authority and courts. Dutch authorities said cyberattacks hit...
China-linked group UNC3886 targeted Singapore ’s telecom sector in a cyber espionage campaign, Singapore’s Cyber Security Agency revealed. Cyber Security Agency of Singapore (CSA) and...
In the latest development, Banana Gun tames the 100,000 TPS beast with the MegaETH Mainnet Live as the “Best Crypto Trading Bot” infrastructure from day...
The European Commission is investigating a cyberattack after detecting signs that its mobile device management system was compromised. The European Commission is investigating a cyberattack...
You probably think the security mantra “you can’t protect what you don’t know about” is an inarguable truth. But you would be wrong. It doesn’t...
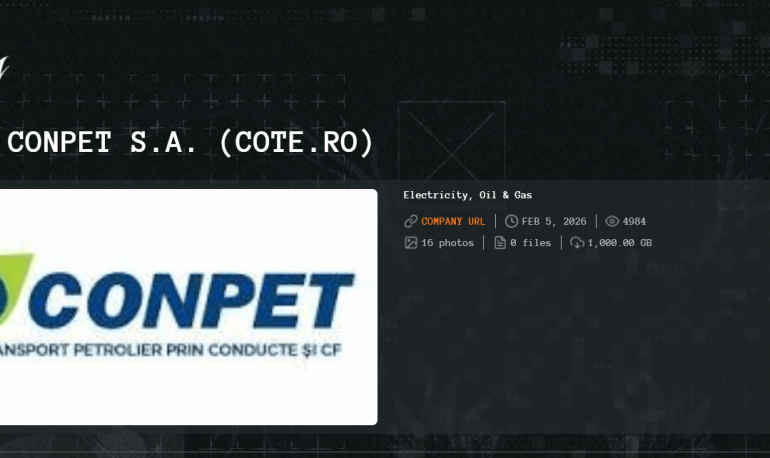
Romania’s national oil pipeline operator Conpet said a cyberattack disrupted its business systems and temporarily knocked its website offline. Conpet is a state-controlled company that...
In this post, I will talk about the features, pros, and pricing for the 7 best mapping platforms. Pinning a few addresses on a map...
A new round of the weekly Security Affairs newsletter has arrived! Every week, the best security articles from Security Affairs are free in your email...
Rome’s La Sapienza University was hit by a cyberattack that disrupted IT systems and caused widespread operational issues. Since February 2, Rome’s La Sapienza University,...
CISA ordered U.S. federal agencies to improve management of edge network devices and replace unsupported ones within 12–18 months. The U.S. Cybersecurity and Infrastructure Security...
Platforms don’t need cookies to track you. Learn how digital fingerprinting works across four layers and practical steps to reduce your exposure. You cleared your...