In this post, I will show you where to get highly rated PowerPoint templates. Whether you plan to pitch a visionary idea to investors, unveil...
In this AI-generated content vs plagiarized content comparison, I will show you what’s the difference and why does it matter? The line between original and...
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds SmarterTools SmarterMail and React Native Community CLI flaws to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity...
In this post, I will discuss 7 logo design tips for startups. In a world where a new startup surfaces every other day, it takes...
In this post, I will show you the top features to look for in Access Control Systems for Indianapolis properties. The janitor used the emergency...
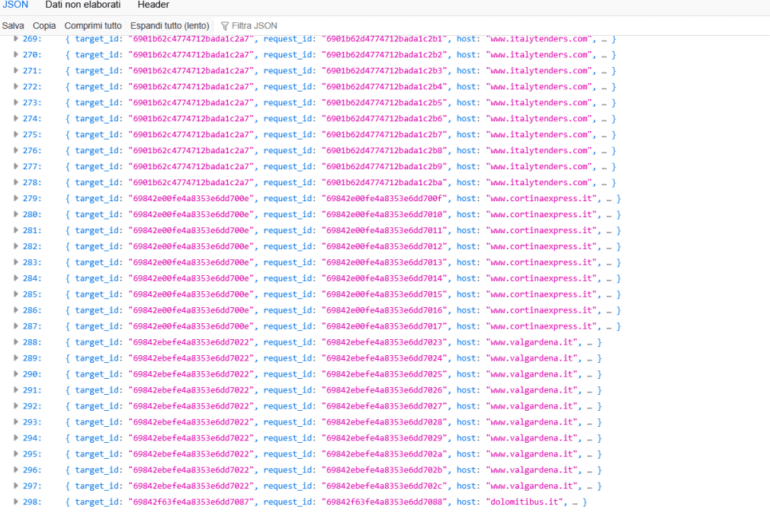
Italy stopped Russian-linked cyberattacks targeting Foreign Ministry offices and Winter Olympics websites and hotels, Foreign Minister Tajani said. Italy has thwarted a series of Russian-linked...
In the latest development, I will show you why Ethereum trading is finally moving to the web – and what Banana Pro changes for ETH...
In this post, I will talk about why you need a trusted San Miguel real estate partner. The allure of San Miguel de Allende is...
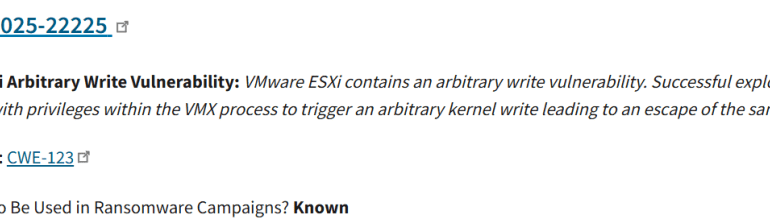
Ransomware groups now exploit VMware ESXi vulnerability CVE-2025-22225, patched by Broadcom in March 2025. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) confirms that ransomware...
In this post, I will talk about the tips to prevent personal data breaches on your website. Websites have become one of the easier places...
In this post, I will talk about grants 101 and where nonprofits, small businesses, and individuals should look first. For nonprofits, small businesses, and individuals...
In this post, I will talk about the data behind basketball’s geographic talent pipeline. Every NBA and ABA superstar started somewhere—often in a city park...