Fantasy football in the Philippines has stopped being a quiet side hobby you admit to only when someone asks why you’re staring at a lineup...
Fortinet released fixes for a critical FortiOS SSO auth bypass (CVE-2026-24858) actively exploited, impacting FortiOS, FortiManager, and FortiAnalyzer. Fortinet started rolling out patches for a...
The year 2026 has started with an avalanche of zero-day vulnerabilities, causing a menace for cyber defenders. Right after Microsoft Office zero-day (CVE-2026-21509) and a...
In this Gold & Goblins guide, I will show you how to mine, merge Goblins, and build a powerful empire. Gold & Goblins is a...
Here is a practical guide to finding a secure online casino in France. Learn how to verify licenses, use local payment methods like Neosurf, and...
In this post, I will talk about how Retrofitting is redefining scalability in modern automation systems. Everyone loves to talk about greenfield automation projects. Fresh...
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Microsoft Office, GNU InetUtils, SmarterTools SmarterMail, and Linux Kernel flaws to its Known Exploited Vulnerabilities catalog. The U.S....
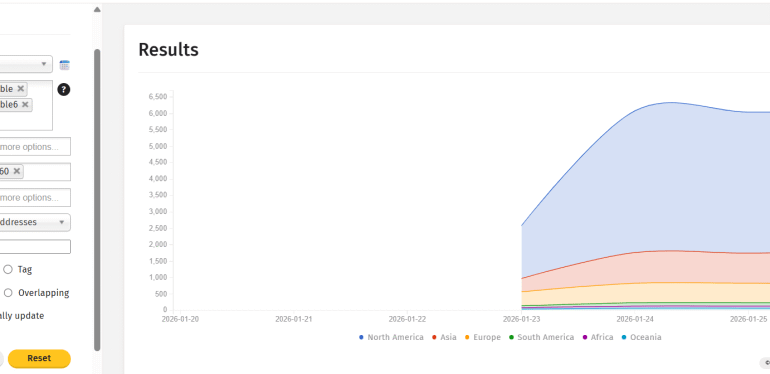
Shadowserver researchers found 6,000+ SmarterMail servers exposed online and likely vulnerable to a critical auth bypass flaw. Nonprofit security organization Shadowserver reported that over 6,000...
Shortly after its January Patch Tuesday release, addressing 114 vulnerabilities, including a zero-day in Windows Desktop Manager (CVE-2026-20805), Microsoft rushed out an emergency out-of-band update...
Crunchbase confirms a data breach after cybercrime group ShinyHunters claims to have stolen over 2 million personal records. Crunchbase confirmed a data breach after the...
In this post, I will talk about balancing price and exclusivity with dedicated DC proxies. In today’s data-driven digital landscape, proxies aren’t just tools—they’re lifelines...
In this post, I will talk about VPN for PC. Read on as I guide you through security, privacy, and performance. These days, our PCs...