DENVER, Colo. – April 27, 2022 – StackHawk, the company making application security testing part of software delivery, has released its official integration with Snyk,...
Marc Prioleau – The Complexity of Massively Distributed Mapping Technology opsdemon Mon, 29/04/2024 – 09:00 Marc Prioleau of the Overture Maps Foundation discussed the solution...
Your Must-Know AI and Cloud-Native AppSec Insights at RSAC 2024 opsdemon Mon, 29/04/2024 – 09:00 Are you looking to catch up on the latest in...
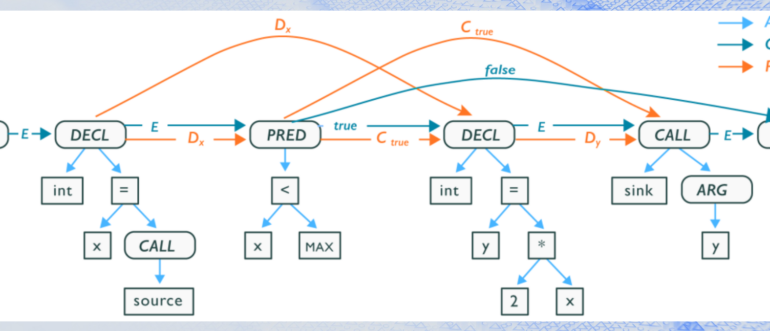
In the ever-evolving landscape of software development, ensuring the security of applications has become a paramount concern. As cyber threats continue to grow in sophistication,...
Qwiet AI and the ancient Greek physicians like the father of medicine Hippocrates have much in common. Hippocrates highlighted the significance of a healthy diet...
The What and Why of Cloud Detection and Response opsdemon Thu, 25/04/2024 – 09:00 A recent survey from Gartner forecasts that worldwide end-user spending on...
Cloud Detection and Response Has Evolving, Cloud-Scale Challenges opsdemon Fri, 26/04/2024 – 09:00 In our previous post, we explored the essentials of cloud detection and...
Cloud Unfiltered with Cole Kennedy – Attestation is the Key – Episode 9 opsdemon Mon, 22/04/2024 – 09:00 In the latest episode of Cloud Unfiltered,...
A C-Suite View of Cloud DevSecOps Today and Tomorrow opsdemon Fri, 26/04/2024 – 09:00 Hear about trends of innovative security leaders and how developers and...
Managing Cybersecurity Risk from the CI/CD Pipeline to the Board Room opsdemon Fri, 26/04/2024 – 09:00 In this panel conversation with leaders in cybersecurity, get...
Breaking the Cloud to Build the Cloud opsdemon Fri, 26/04/2024 – 09:00 There’s no such thing as a perfectly secure cloud environment. Vulnerabilities, holes left...
5 Best Open Source Application Security Security Tools in 2024 opsdemon Thu, 25/04/2024 – 09:00 As cybersecurity becomes increasingly important in software development, the “shift...